We're excited to introduce ValidIaC, an open-source tool, inspired by Komodor's ValidKube, to help validate the syntax, security, costs, and graph of your IaC resources. In the same way that ValidKube aggregates best-of-breed open source tools to help ensure Kubernetes YAML best practices, ValidIaC combines four open-source tools for the purpose of Infrastructure-as-Code best practices.
ValidIaC is a new open-source tool that combines several open-source projects and tools to allow developers to check their Terraform HCL (stay tuned for more IaC tools in the near future) code without changing context and from within the same workflow. ValidIaC integrates four popular tools for Terraform to bring the combined value of each tool:
- Lint - tflint, A Pluggable Terraform Linter that finds possible errors (like illegal instance types) and warns about deprecated syntax and unused declarations
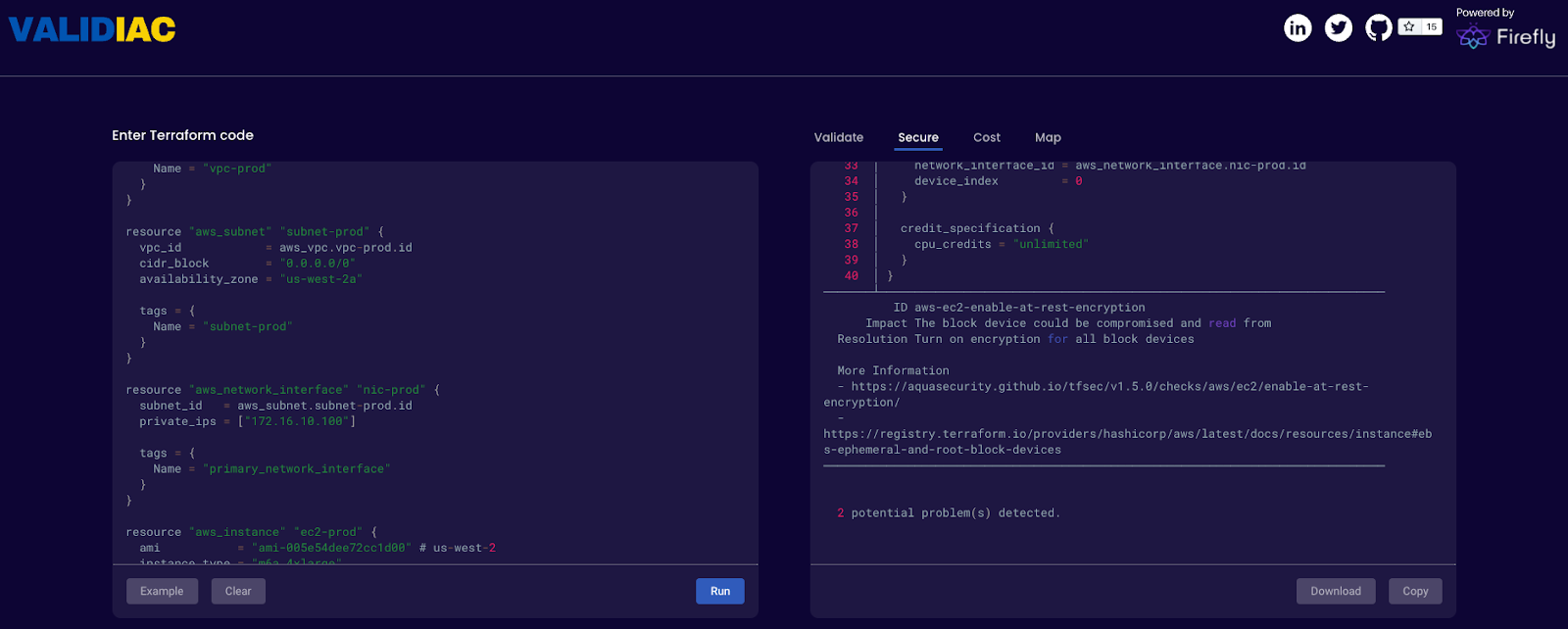
- Security - tfsec uses static analysis of your Terraform templates to spot potential security issues.
- Cost - infracost, shows cloud cost estimates for Terraform, before making changes to the cloud.
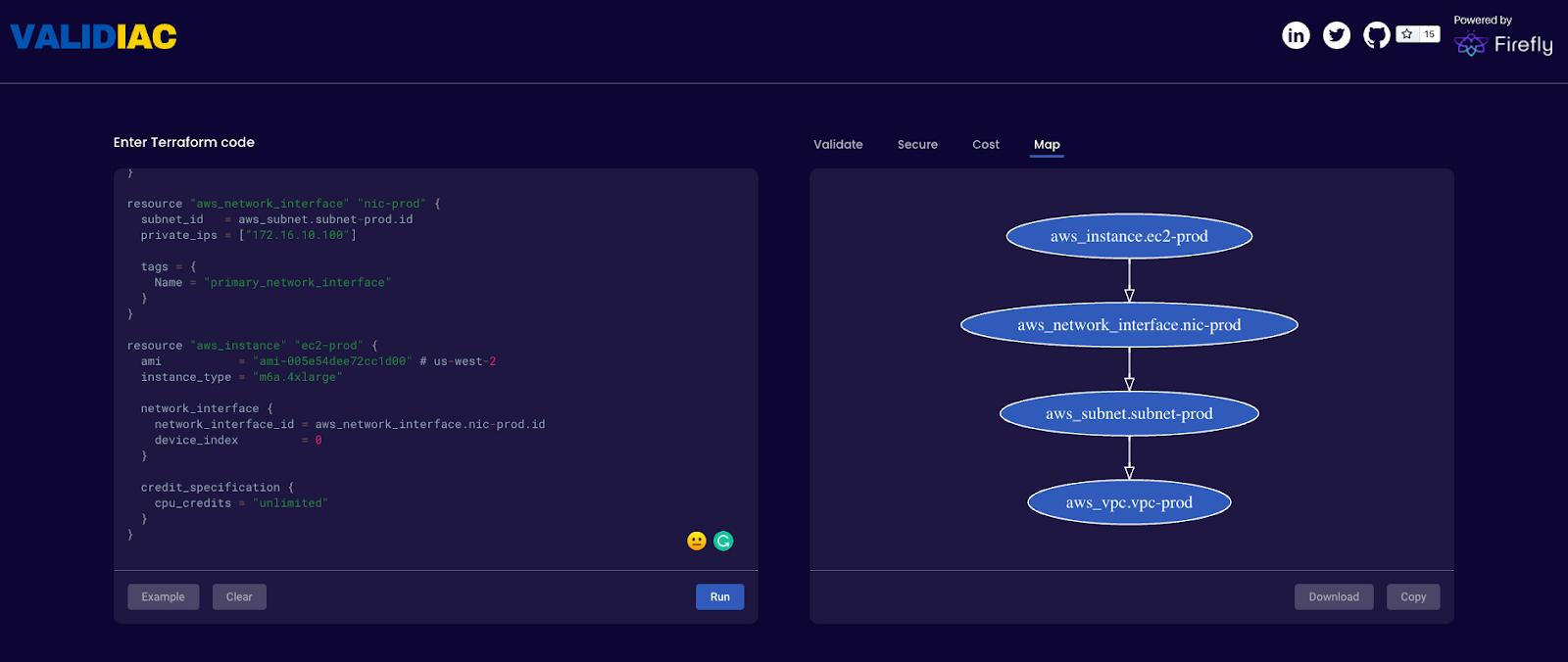
- Mapping - inframap reads your tfstate or HCL to generate a graph specific for each provider, showing only the resources that are most important/relevant.
This makes it possible to leverage the power of these four tools in a single place, at any time, directly from your browser to provide DevOps, SRE, and Cloud teams with peace of mind when deploying and managing Terraform blueprints.
All-in-one IaC Checker
In 2014 HashiCorp introduced Terraform to solve the issue of provisioning complicated infrastructure – bringing together worlds of multiple cloud providers. But in reality, provisioning Terraform and making sure that your code is compliant with best practices, both from a technical and security perspective, is no easy task. This is why the community of its users has built many useful open-source tools to help cope with the diversity of challenges with IaC.
However, the sheer number of tools and projects available is daunting and can be overwhelming to a DevOps Engineer who simply wants to make sure that their infrastructure is aligned with the company’s security goals, budget, and technical requirements.
Why We Decided to Build ValidIaC
I’ve seen firsthand the challenges developers face when deploying to the CI/CD. In my experience, it takes a while to gather all the skillset and tools required to make sure that your code is optimal in terms of cost, syntax, and security.
As a CTO and a developer myself, I knew the value that members of the community could get from using a tool that simplifies this entire process. When I first encountered Komodor’s open-source project ValidKube and tried it out, I quickly realized what value it gives to developers and wanted to create a sister project that will enable a similar value in the context of Infrastructure-as-Code.
How it Works
ValidIac is straightforward - you first drop your Terraform code in the dedicated area and then press “Run” to see the magic happen in 4 categories: Validate (lint), Secure, Cost, and Map.
Validate

Secure
Cost

Map
Try it Yourself
Check out ValidIaC here to get started, and benchmark your code against industry best practices.
ValidIaC currently supports Terraform HCL, however, support for CloudFormation and Pulumi will be introduced in the near future. ValidIaC is an open-source tool, so community contributions are most welcome to add more tools or capabilities that can benefit the community.
